Introduction to User and Role Permissions
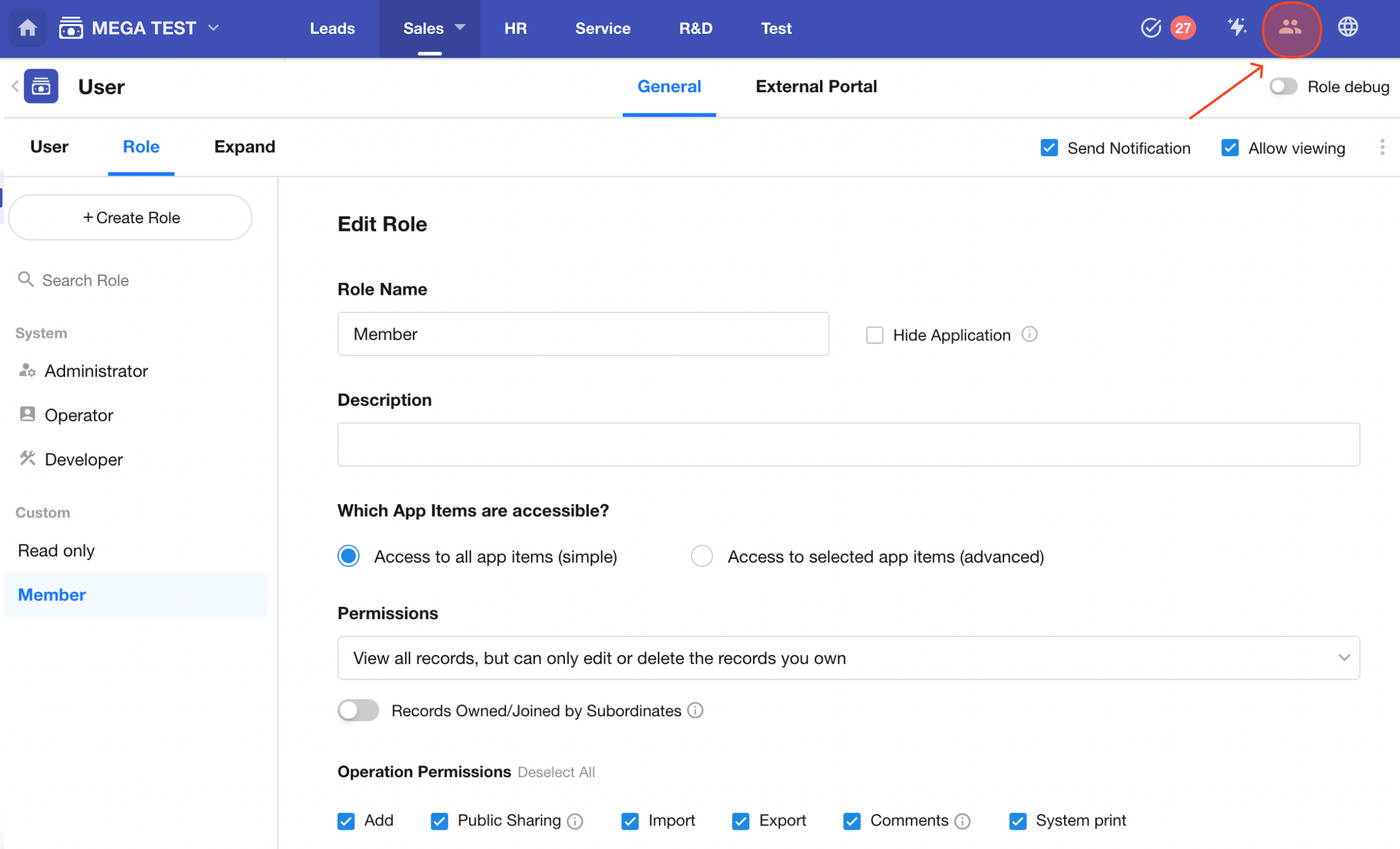
Collaboration between multi-role users is essential in enterprise applications. Each role may have different levels of access to enterprise data. The permission configuration in the application is highly granular and supports custom setups to ensure that users have the appropriate operational permissions.
Permission Logic for Users
User permissions are associated with roles. You first define permissions for a specific role, and then assign the role to users. Users gain permissions by being members of one or more roles. This Role-Based Access Control (RBAC) model ensures clarity and ease of management.
With role-based permission settings, you can implement the following scenarios:
-
The application includes multiple worksheets, and users can only access specified worksheets.
-
Within a worksheet, users can only view designated views.
-
Within a view, users can only see the records they created.
-
Users can view all records but are only allowed to edit or delete those related to themselves.
-
When viewing a record, some fields are hidden from the user.
-
When editing data, some fields are editable while others are read-only.
-
When adding a new record, users are only allowed to fill in specific fields.
-
Users are restricted from performing certain actions such as sharing or printing when viewing records.